Y-Not-CTF - MadCow
The binary ask for an input and do a ton of computation on it. solved using an angr script.
Description
Take your time to solve this one until the end of the CTF…
Details
Points: 474
Category: reverse
Validations: 4
Solution
We were given a file called MadCow_3ad6db829e62619f19a299086c0f22cf94b36903.
After launching the file a nice cow in ascii art was shown.
/ \
((__-^^-,-^^-__))
`-_---' `---_-'
<__|o` 'o|__>
\ ` /
): :(
:o_o:
"-" 03:19:05 remaining, take your time!!!
what
Nope, Try again!
Opening the file in ida pro shown a mess of calculation on the input.
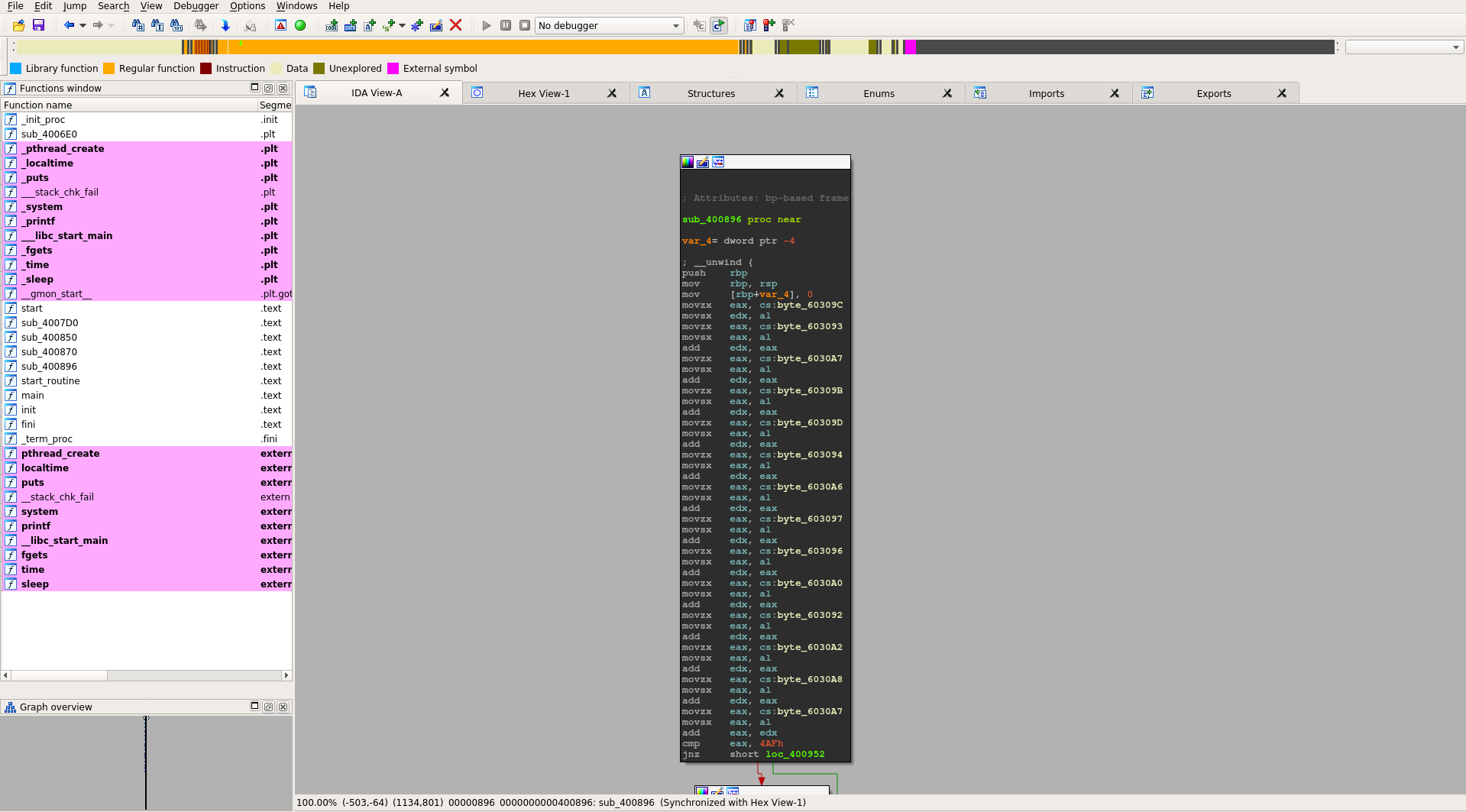
It seems that is a nice candidate for angr.
We wrote a simple python script to bruteforce the flag.
import angr, simuvex, logging
logging.basicConfig(level=logging.DEBUG)
p = angr.Project('./MadCow_3ad6db829e62619f19a299086c0f22cf94b36903', load_options={'auto_load_libs': False})
ex = p.surveyors.Explorer(find=(0x0401C4D, ),avoid=(0x0401C54,))
res = ex.run()
for i in res.found:
print i.state.posix.dumps(0)
Running the script for 10 seconds give us the flag: YNOT17{4ngR_1ntr0duCt10n}.
Challenges resources are available in the resources folder
Written on November 17, 2017
